Community resources
Community resources
Community resources
How to Enable Single Logout (SLO) in Atlassian Data Center applications
What is Single Logout (SLO)
Do you always close your session in Jira when you've finished tracking your work? I seriously doubt it.
Most users regularly forget to log out of their applications when they're done using them, and Atlassian tools are certainly no exception.
In single sign-on environments, that can be particularly true: since users only log in once, they may not be aware of how many open sessions they're running simultaneously.
That's why most SSO solutions include single logout in their offering. The principle is always the same: log out of one application, and the system will take care of shutting every other open session at the same time. Close your session in the Identity Provider (IdP), and all open applications will be automatically shut down.
Unfortunately, Single Logout is not included in the Data Center SSO features, so even if you have it set up on your Okta, Azure AD, or whatever the IdP of your choice is, users of Atlassian applications will not be benefitting from it.
Unless you want to embark into a custom-made solution, the Atlassian Marketplace offers SSO apps that can do the trick. In this article I'm going to give an example and show how you can enable SLO with resolution's SAML SSO apps (for full disclosure, resolution is my current employer).
SAML SSO is available for Jira, for Confluence, and all other main Atlassian products.
Why not logging out is dangerous
But first, let me give a short reminder of why leaving sessions open is a really bad habit from a security standpoint.
When user sessions in Jira, Confluence, Bitbucket or any other Atlassian, you are vulnerable to at least two types of malicious attacks:
- Session hijacking, which is relatively simple and can be achieved for example by sniffing the active session token. If successful, the attacker will have access to the Web Server.
- One-click attacks, or Cross-Site Request Forgeries (CSRF), which trick the user into taking an action he wouldn't normally do with social engineering techniques. Yes, it's far-fetched. But if you have compliance proccesses or millionaire business approvals on Jira, someone might actually take a shot.
How to configure Single Logout in Atlassian applications
The following steps work for Jira, Confluence, Bitbucket, Bamboo, or Fisheye applications in both Data Center and Server hostings.
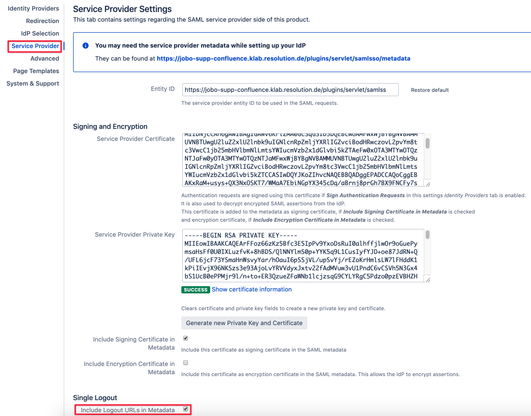
Step 1: Include the Single Logout URLs in the SAML Metadata
To include the SLO URLs in the SAML Metadata, simply check the box at the bottom in the Service Provider tab
There are two options here:
- Inside the plugin: Check the corresponding option in the Service Provider tab of the configuration menu
- In the Identity Provider: Paste this URL in the IdP's metadata:
https://<baseUrl>/plugins/servlet/samlsso/metadata?slo
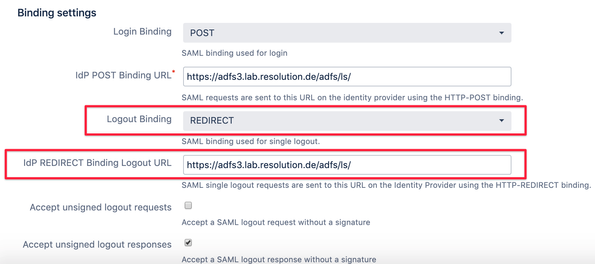
Step 2: Choose your preferred option for the Logout Binding.
Go to the Identity provider tab and choose between POST and Redirect.
This step will determine the exact format for exchanging data between your IdP and your Atlassian applications.
Step 3: Load the SLO URL in resolution's app
In the same tab, make sure that the SLO URL is already loaded; if not, go ahead and set it using the format in Step 1.
Step 4: Save the configuration
Step 5: Configure the IdP
Now it's time to check the settings in your IdP to make sure it fully supports your setup.
While settings will vary for each IdP, you can see a detailed explanation here for the most common Identity Providers:
For additional details, have a look at the full documentation.
Conclusion
Single Logout is an integral component of a full SSO solution that you'll want to set up to protect your corporate assets. Resolution's SAML SSO apps will help you set it up for both Server and Data Center hostings of your Atlassian applications.
Remember that whether SLO is possible will ultimately depend of your IdP. Although leaders in the IAM landscape include this possibility, other minor providers or custom-develop solutions may not have Single Logout capabilities.
Was this helpful?
Thanks!
Capi [resolution]
About this author
Inbound Marketing | Thought Leadership
Resolution
Berlin, Germany
19 accepted answers
Atlassian Community Events
- FAQ
- Community Guidelines
- About
- Privacy policy
- Notice at Collection
- Terms of use
- © 2025 Atlassian





0 comments