Community resources
Community resources
Community resources
- Community
- Products
- Confluence
- Questions
- Ssl error: java.net.UnknownHostException:https
Ssl error: java.net.UnknownHostException:https
Hi,
Specs:
Server 2016
Java (32bit) Version 8 Update 151
We installed Atlassian Confluence on premises and would like to communicate to it using SSL.
Atlassian has a nice manual that we carried out.
We have a wildcard certificate (Comodo) that we wanted to use for this.
So, we created a keystore, imported the certificate (.crt) and pointed the server configfile to it:
<Connector port="8443" maxHttpHeaderSize="8192"
maxThreads="150" minSpareThreads="25"
protocol="org.apache.coyote.http11.Http11NioProtocol"
enableLookups="false" disableUploadTimeout="true"
acceptCount="100" scheme="https" secure="true"
clientAuth="false" sslProtocols="TLSv1,TLSv1.1,TLSv1.2" sslEnabledProtocols="TLSv1,TLSv1.1,TLSv1.2" SSLEnabled="true"
URIEncoding="UTF-8" keystorePass="password"
keystoreFile="D:\somepath\atlassian"
/>
Than we downloaded the root and intermediate certificates from Comodo and imported them in the cacerts store.
After that we restarted the Atlassian Confluence service.
We connect to Confluence using this url: https://app##.domain.local:8443
When we use Chrome we get an: ERR_SSL_VERSION_OR_CIPHER_MISMATCH error
When we use Firefox we get a: SSL_ERROR_NO_CYPHER_OVERLAP error.
We used a nifty tool to import the certificates: KeyStore Explorer.
This little tool has also an option: Examine SSL.
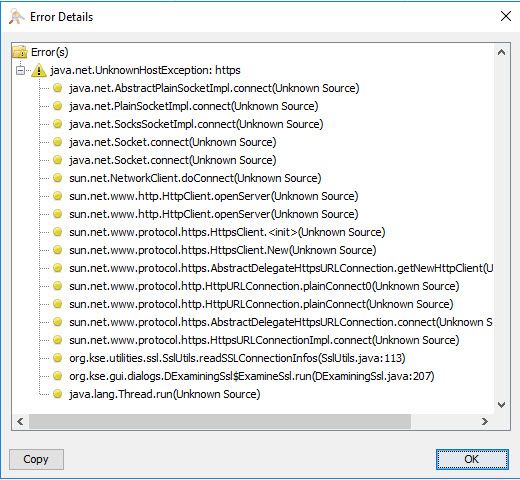
It gives us this error:
What are we doing wrong and how can we fix this ?
Any help is appreciated !
Thanks in advance.
1 answer
Hello,
Possibly the following would help, if you use the conversion process to include both crt and private key in generating a PKCS12:
Convert the existing cert to a PKCS12 using OpenSSL. A password is required when asked or the 2nd step will complain.
openssl pkcs12 -export -in [my_certificate.crt] -inkey [my_key.key] -out [keystore.p12] -name [new_alias] -CAfile [my_ca_bundle.crt] -caname root
Convert the PKCS12 to a Java Keystore File.
keytool -importkeystore -deststorepass [new_keystore_pass] -destkeypass [new_key_pass] -destkeystore [keystore.jks] -srckeystore [keystore.p12] -srcstoretype PKCS12 -srcstorepass [pass_used_in_p12_keystore] -alias [alias_used_in_p12_keystore]
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.

Was this helpful?
Thanks!
- FAQ
- Community Guidelines
- About
- Privacy policy
- Notice at Collection
- Terms of use
- © 2025 Atlassian





You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.