Community resources
Community resources
aws-ecr-push-image pipe adding bitbucket environment variables including encrypted values with image
Hello,
I am currently using the aws-ecr-push-image pipe to push my docker images to the elastic container registry. i see that when the pipe runs, all the environment variables that I stored on my bitbucket account are being attached to the image as build arguments.
I think this is a security issue since we have some variables which are supposed to be secrets and only used by bitbucket pipelines but these are instead getting attached to the docker image when getting pushed to the ECR.
So that means, anyone who uses that image can basically see those secrets when they use the container.
2 answers
1 accepted
Hi @Bharath Singireddy ,
Thanks for reaching out. Let me clarify your concerns:
Security model in pipes
I see that when the pipe runs, all the environment variables that I stored on my bitbucket account are being attached to the image as build arguments
That's not accurate. We are only passing the required environment variables for the pipe to run:
- Default Pipelines system environment variables: https://support.atlassian.com/bitbucket-cloud/docs/variables-in-pipelines/ such as BITBUCKET_COMMIT or BITBUCKET_BUILD_NUMBER. They are always passed by default.
- Variables that are defined as pipe arguments, such as IMAGE_NAME or TAG for the aws-ecr-push-image pipe.
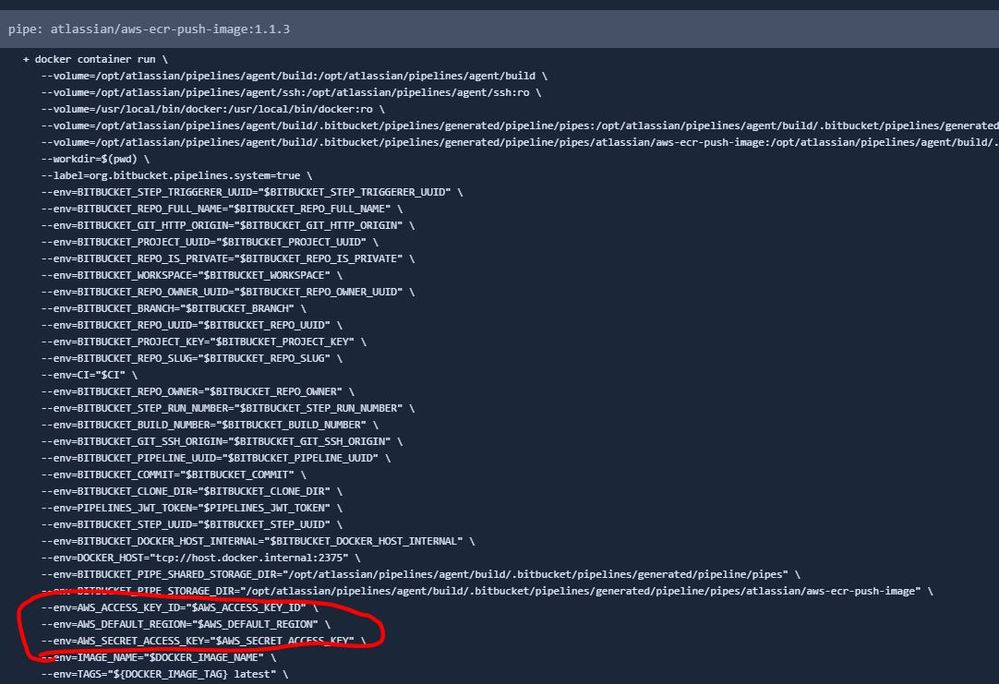
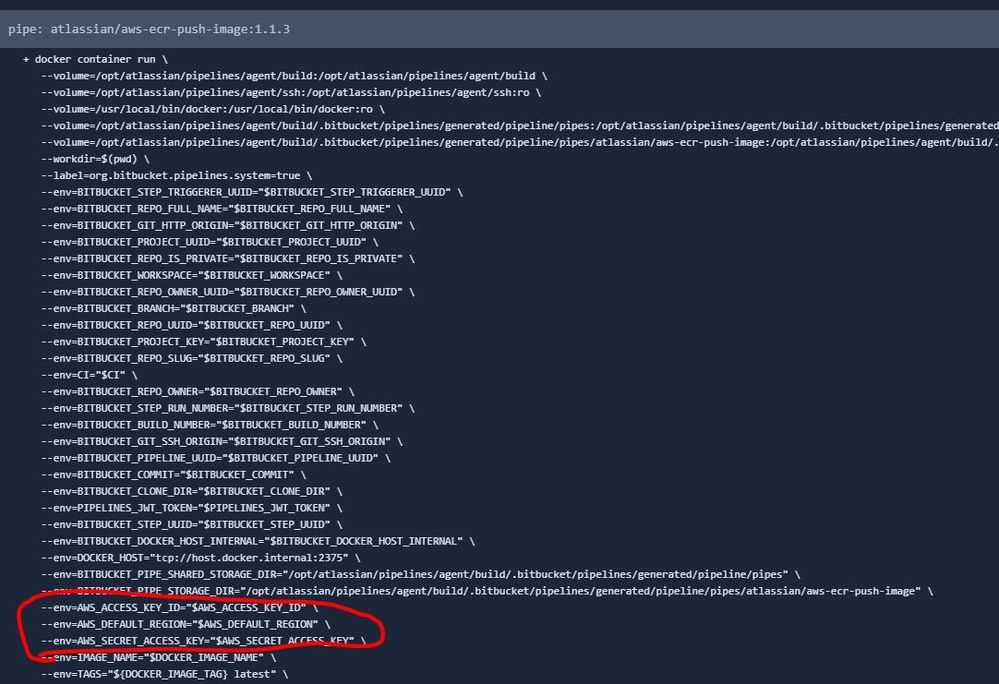
- Default pipe variables defined by pipe authors. For AWS pipes, pipes authors configured to automatically pass AWS_ACCESS_KEY_ID, AWS_SECRET_ACCESS_KEY and AWS_DEFAULT_REGION, to improve user experience and avoid passing all three variables repeatedly.
So, talking about secrets, only AWS secrets are passed to the aws-ecr-push-image, which are required to authenticate to AWS to be able to execute the script that pushes the image: https://bitbucket.org/atlassian/aws-ecr-push-image/src/master/pipe/pipe.py.
It's important to note that we are passing the variables as environment variables to docker run command (runtime): https://docs.docker.com/engine/reference/commandline/run/#set-environment-variables--e---env---env-file. not as build arguments. So, we are not building the docker image (nor pushing it), we are just executing it passing the required env variables to an image that already exists: https://hub.docker.com/r/bitbucketpipelines/aws-ecr-push-image.
So that means, anyone who uses that image can basically see those secrets when they use the container.
That's not right. The docker container for the pipe is executed locally in Pipelines, so the secrets (AWS_ACCESS_KEY_ID, AWS_SECRET_ACCESS_KEY, AWS_DEFAULT_REGION) are not leaving Bitbucket Pipelines at any point.
For all those reasons, the pipes model is totally secure, and provides even better isolation as pipes only get the secrets they need to run.
Theory
For your particular case (aws-ecr-push-image), I think you might probably be confusing the docker image you build with the pipe you use to push that docker image to ECR. For example:
# build the image - docker build -t my-docker-image . # use the pipe to push the image to AWS ECR - pipe: atlassian/aws-ecr-push-image:1.1.3 variables: IMAGE_NAME: my-docker-image
- When you build the docker image (called my-docker-image in the example) you decide what build arguments you need to pass to build it. In this case, it's up to you to make sure you don't add secrets, SSH keys as build arguments to the docker image.
- When you execute the pipe command, internally we only push the image that you built previously (specified as parameter), so no secrets are passed to your previously built image.
Hopefully I clarified your concerns about this. Feel free to check the source code here: https://bitbucket.org/atlassian/aws-ecr-push-image/src/master/ if you want to know more about how the ECR pipe works.
Let me know if you have any other questions, I'll be happy to help.
Regards,
Raul
Hello,
@Raul Gomis
Thanks for the detailed answer.
I think it was my bad that I didn't check it.
I didn't notice that it was the docker run command that the environment variables are being attached too.
i was in an assumption that it was adding it to the image that we want to push to ECR.
Anyways thanks again for clear and detailed answer
Regards
Bharath Singireddy
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.

Was this helpful?
Thanks!
- FAQ
- Community Guidelines
- About
- Privacy policy
- Notice at Collection
- Terms of use
- © 2024 Atlassian





You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.