Community resources
Community resources
Community resources
Let's check installed app dependency to be compliant for OWASP Dependency-Check
Hi!
Nowadays. security and trust is a very important aspect. I was wondering a lot of administrators, security specialists, security researches and attackers investigate installed components on the production system, e.g. Jira opened through the internet.
To minimize the risk you can investigate the jar files in directory installed plugins, the same thing I can do for every Atlassian product installed in your company.
I'd like to share very small tip and trick related dependency checker and I hope you will check your set of installed apps or developed apps.
next part you can find (here PART-2)
1. Introduction
Just a small quote which shows important from OWASP site.
Dependency-Check is a utility that identifies project dependencies and checks if there are any known, publicly disclosed, vulnerabilities
Also, keep in your mind it is not deep analysis, instead of using static code analyzers Sonar, PVS studio, but it provides a good overview and possibility to raise an issue to app vendor.
2. Steps for already installed apps
2.1. Just prepare files from production the latest snapshot of installed plugins
tar -czvf apps.tgz {jira_home}/plugins/installed-plugins
scp apps.tgz localpc:/tmp/2.2. Next step extracts, install and run checks on MacOS.
$ tar -xzvf apps.tgz
$ brew update && brew install dependency-check
$ dependency-check --project Testing --out . --scan apps// output will be like this
[INFO] Checking for updates
[INFO] starting getUpdatesNeeded() ...
[INFO] NVD CVE requires several updates; this could take a couple of minutes.
[INFO] Download Started for NVD CVE - 2010
.....
[INFO] Download Started for NVD CVE - 2019
[INFO] Download Complete for NVD CVE - 2010 (16588 ms)
[INFO] Download Complete for NVD CVE - 2011 (21166 ms)
[INFO] Download Complete for NVD CVE - 2017 (22498 ms)
[INFO] Download Complete for NVD CVE - 2019 (8438 ms)
[INFO] Processing Complete for NVD CVE - 2018 (45473 ms)
[INFO] Begin database maintenance.
[INFO] End database maintenance.
[INFO] Check for updates complete (96830 ms)
[INFO] Analysis Started
[INFO] Finished Archive Analyzer (15 seconds)
[INFO] Finished File Name Analyzer (0 seconds)
[INFO] Finished Jar Analyzer (2 seconds)
[INFO] Finished Central Analyzer (32 seconds)
[INFO] Finished Dependency Merging Analyzer (0 seconds)
[INFO] Finished Version Filter Analyzer (0 seconds)
[INFO] Finished Hint Analyzer (0 seconds)
[INFO] Created CPE Index (1 seconds)
[INFO] Skipping CPE Analysis for npm
[INFO] Finished CPE Analyzer (4 seconds)
[INFO] Finished False Positive Analyzer (0 seconds)
[INFO] Finished NVD CVE Analyzer (3 seconds)
[INFO] Finished Vulnerability Suppression Analyzer (0 seconds)
[INFO] Analysis Complete (163 seconds)
You can follow related for your OS instructions from here
3. Review report
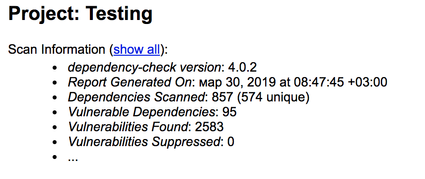
Today I did the fresh report for 93 installed apps.
3.1. In dependency-check-report.html you can find first overview like this
3.2. In the report you can find the link "How to read the reports" and some things were interesting like that in below a screenshot
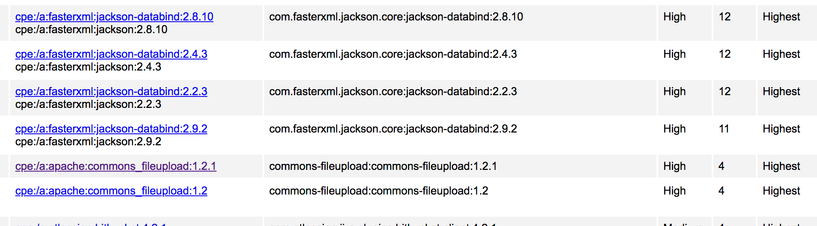
3.3. Review plugin by plugin.
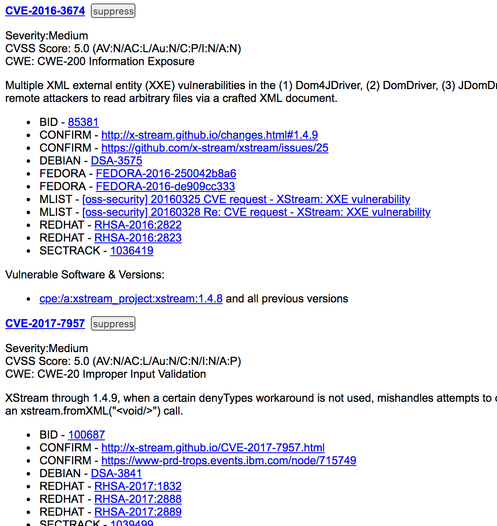
If you click in the report to plugin jar file you will find all related check results with CVE. e.g.
4. What about in-house apps?
Let's add into your pom.xml. Because everything did it before us.
<project>
...
<build>
...
<plugins>
...
<plugin>
<groupId>org.owasp</groupId>
<artifactId>dependency-check-maven</artifactId>
<version>5.0.0-M2</version>
<executions>
<execution>
<goals>
<goal>check</goal>
</goals>
</execution>
</executions>
</plugin>
...
</plugins>
...
</build>
...
</project>More detail info you can find here: https://jeremylong.github.io/DependencyCheck/dependency-check-maven/
Conclusion:
- Use the latest versions of apps
- I hope we will check our installed Atlassian ecosystem continuously using CI/CD.
- Raise issues or provide feedback to app vendors after double checks, (false positive can be as well)
- Sleep better a little bit after that :)
All that things was did on Jira 7.6.12, with latest installed apps.
P.S. Next part you can find (here PART-2)
Cheers,
Gonchik Tsymzhitov
Was this helpful?
Thanks!
Gonchik Tsymzhitov

About this author
Solution architect | DevOps
:)
Cyprus, Limassol
175 accepted answers
TAGS
Atlassian Community Events
- FAQ
- Community Guidelines
- About
- Privacy policy
- Notice at Collection
- Terms of use
- © 2025 Atlassian





1 comment