Community resources
Community resources
Community resources
- Community
- Q&A
- Statuspage
- Articles
- Statuspage SSO with Microsoft Entra(Azure AD)
Statuspage SSO with Microsoft Entra(Azure AD)
This article goes over how to setup SSO with Microsoft Entra for Audiance-specific pages
Instructions
Add StatusPage from the gallery
To configure the integration of StatusPage into Microsoft Entra, you need to add StatusPage from the gallery to your list of managed SaaS apps.
-
Sign in to the Azure portal using either a work or school account or a personal Microsoft account.
-
On the left navigation pane, select the Microsoft Entra ID service.
-
Navigate to enterprise Applications and then select All Applications.
-
To add a new application, select New application.
-
In the Add from the Gallery section, type StatusPage in the search box.
-
Select StatusPage from the results panel and then add the app. Wait a few seconds while the app is added to your tenant.
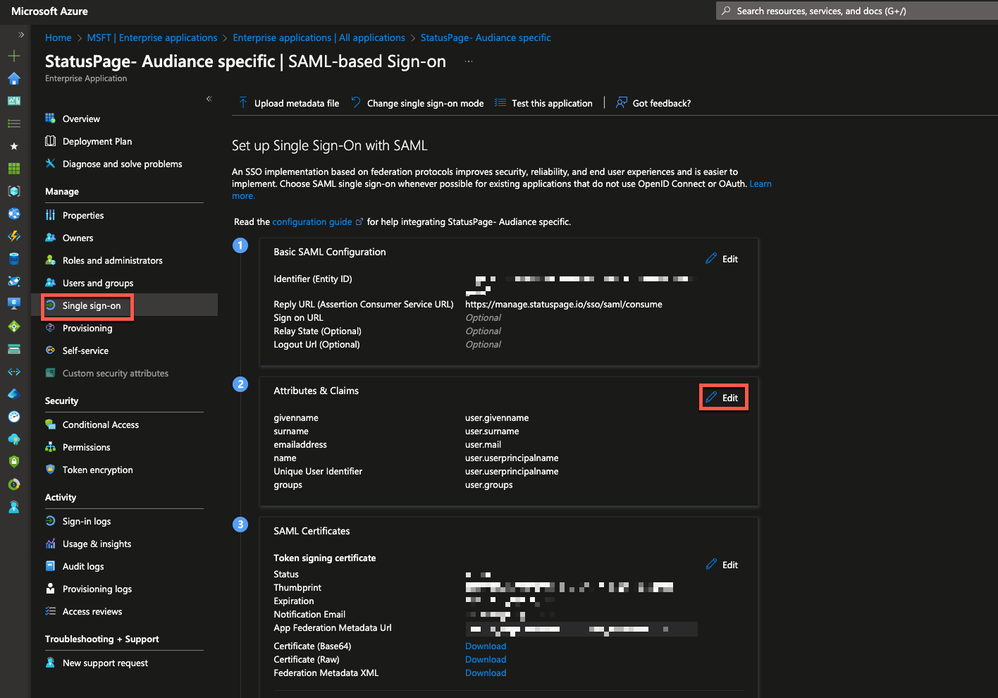
Configure Microsoft Entra ID SSO
Follow these steps to enable Microsoft Entra ID SSO in the Azure portal.
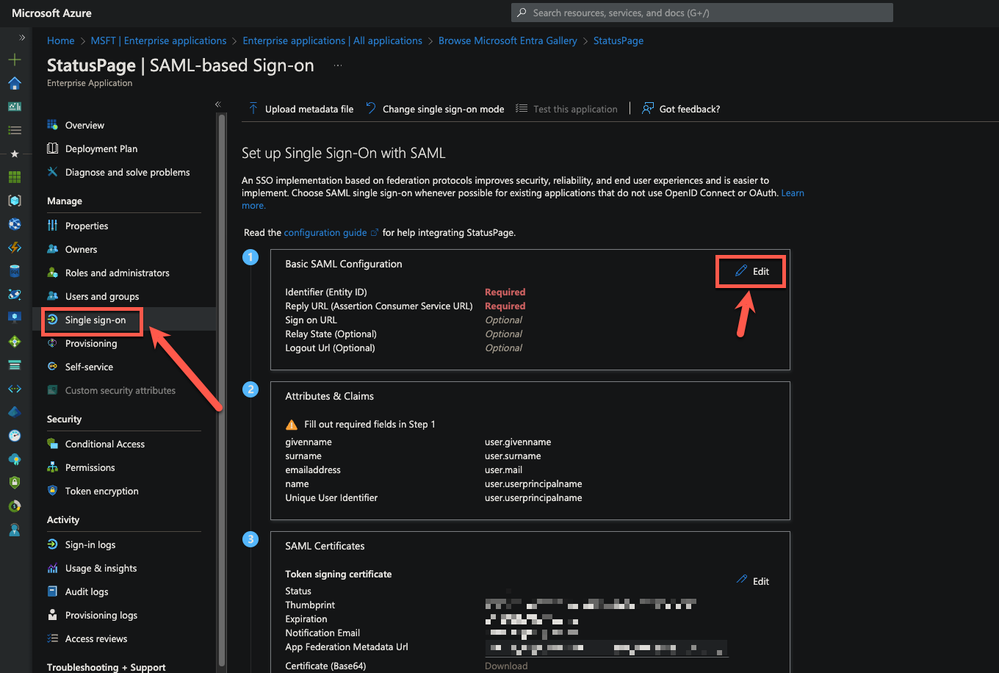
- In the Azure portal, on the Statuspage application integration page, find the Manage section and select single sign-on.
- On the Select a single sign-on method page, select SAML.
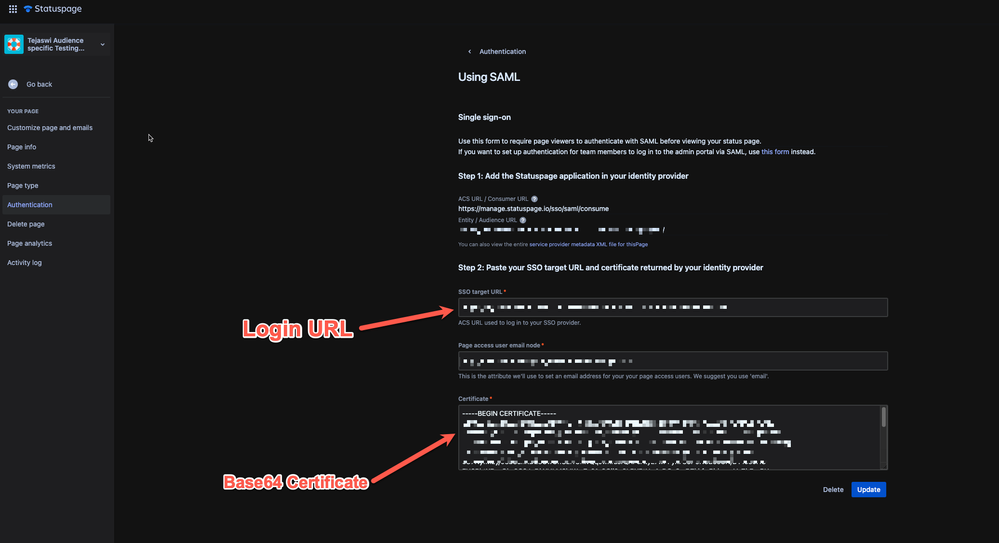
- On the Set up single sign-on with SAML page, click the pencil icon for Basic SAML Configuration to edit the settings.
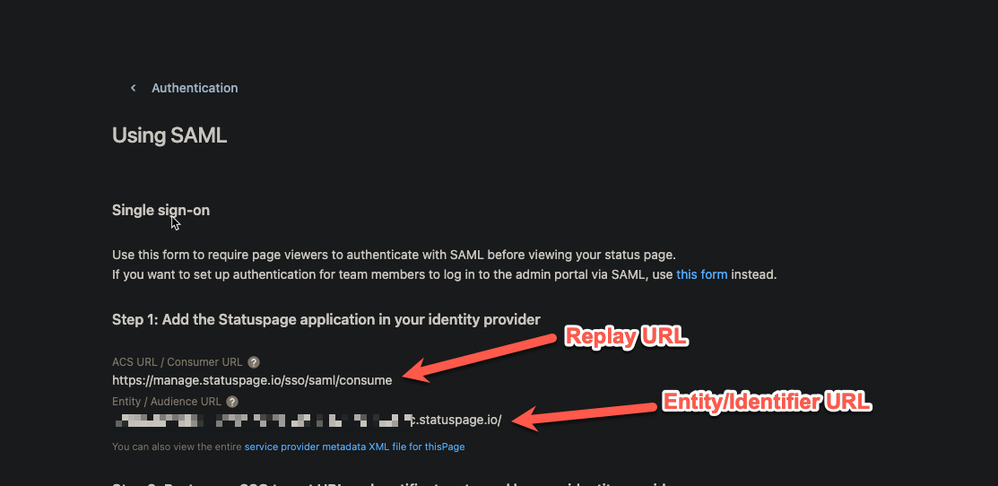
- On the Setup Single Sign-On with SAML page, perform the following steps: a. In the Identifier text box, type an Entity URL from the statuspage b. In the Reply URL text box, Add the below URL from the statuspage.
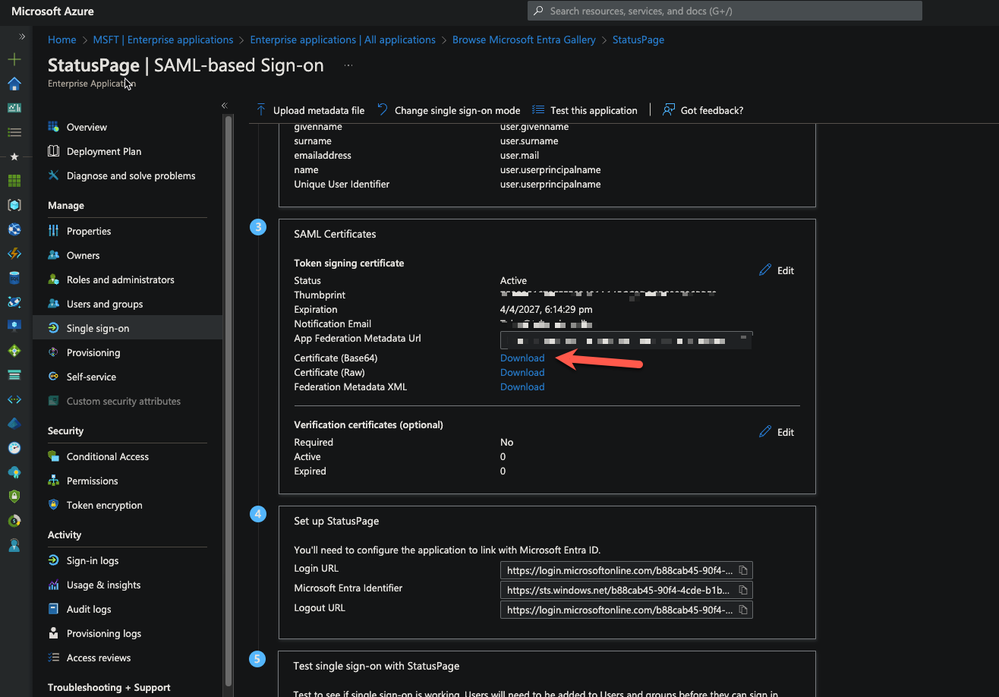
https://manage.statuspage.io/sso/saml/consume - On the Setup Single Sign-On with SAML page, in the SAML Signing Certificate section, click Download to download the Certificate (Base64) from the given options as per your requirement and save it on your computer. Paste the contents of the certificate in the certificate field on the Statuspage.
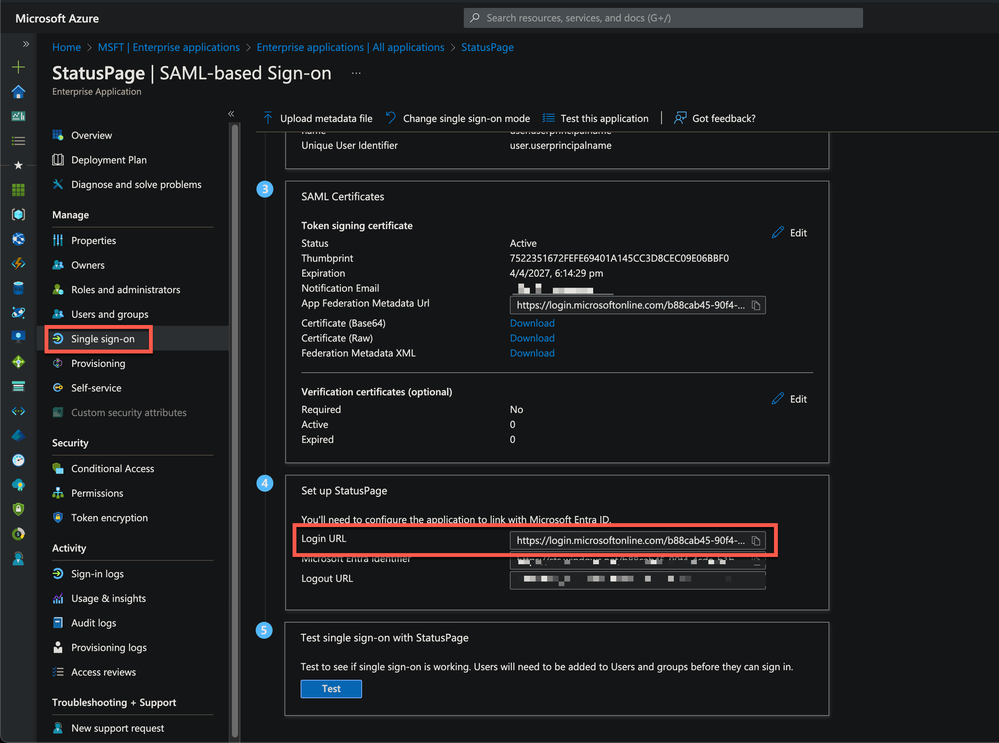
- On the Set up StatusPage section, copy the appropriate URL(s) as per your requirement.
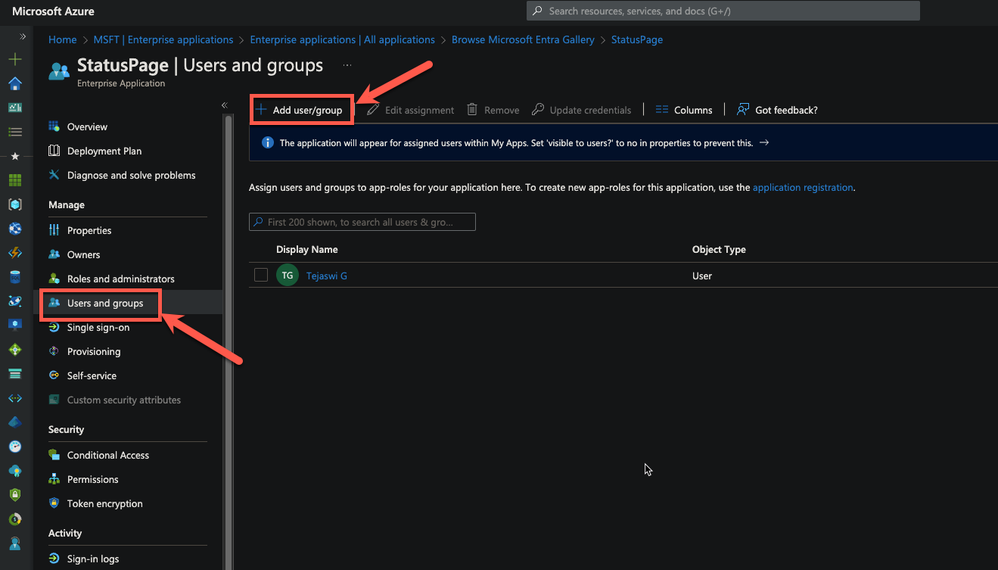
Assign users to the SSO application within Microsoft Azure
- Click on Users & Groups within the Statuspage Application configured in Microsoft Azure.
- Click Add user/group to assign your users to the application.
Configure User email and Group Mappings
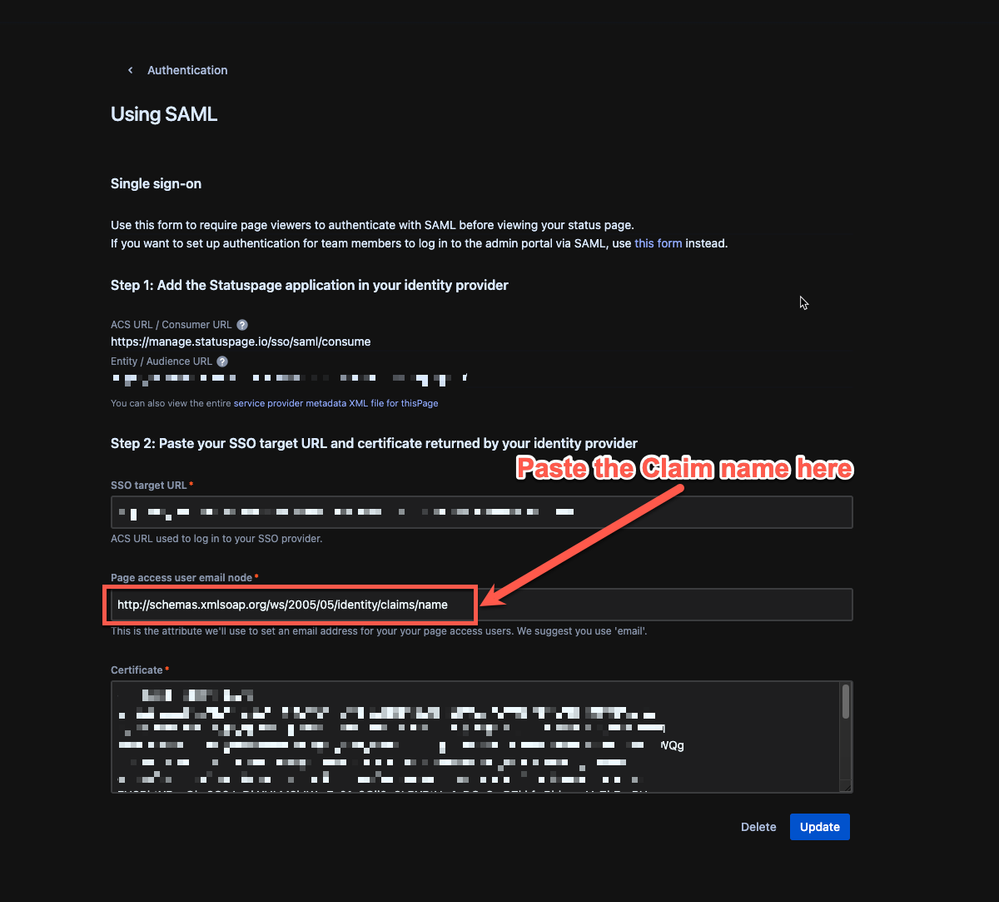
Page access user email note
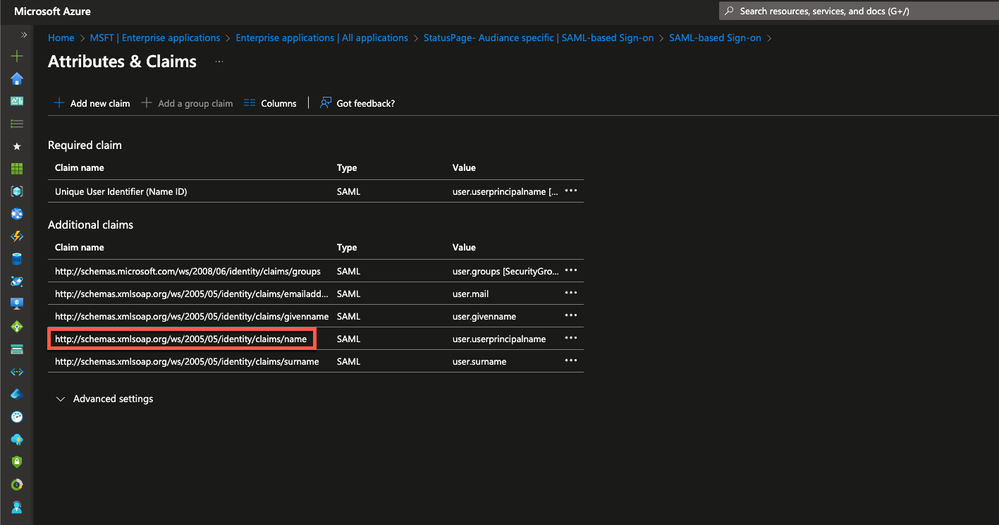
- Within your Microsoft Entra ID SSO setup, there is a section called User Attributes & Claims. Let's open this up and copy the claim name associated with user.userprincipalname. The claim name here is
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name
- Now let's paste the claim name in the Page access user email node field in Statuspage.
Audience Group External identifier
This is how we map groups defined in Microsoft Entra ID over to audience groups in the Statuspage.
-
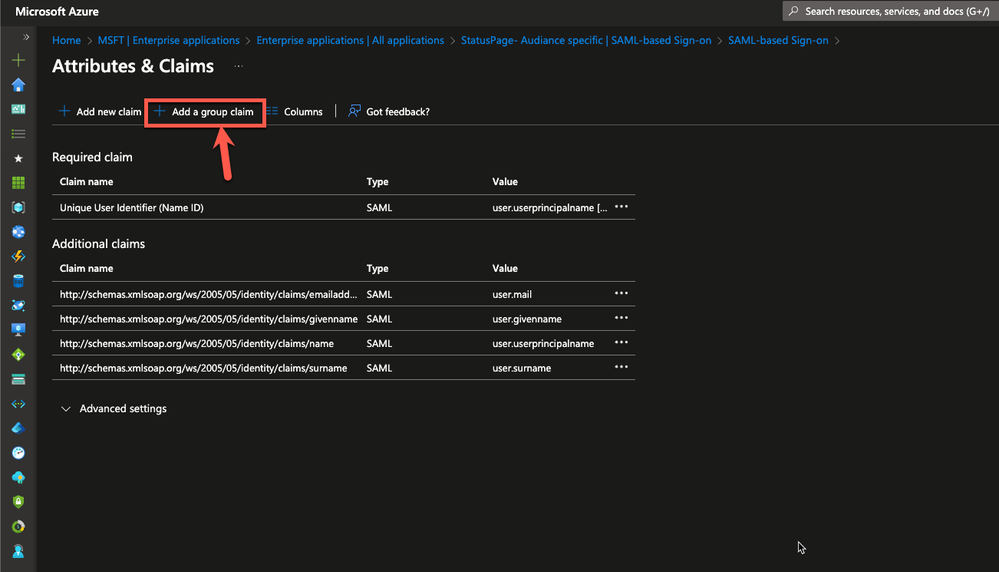
Start with editing the User Attributes & Claims within the SSO configuration of Microsoft Entra ID.
-
Click Add Group claim
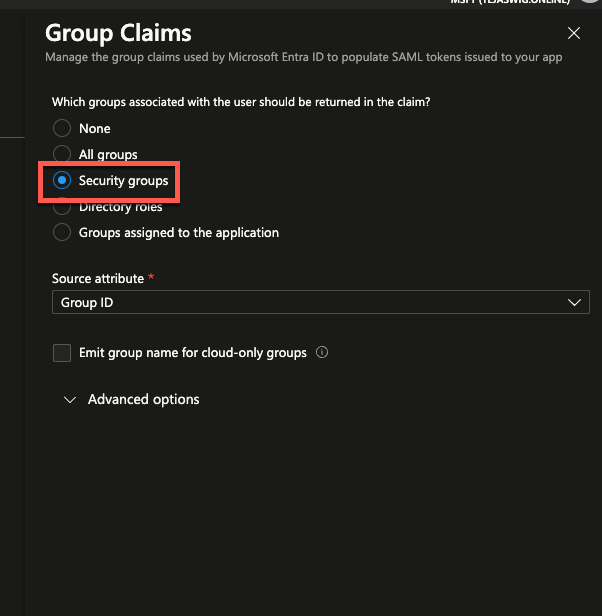
- If you wanted to restrict the groups to just security groups or all, I'm just using security groups.
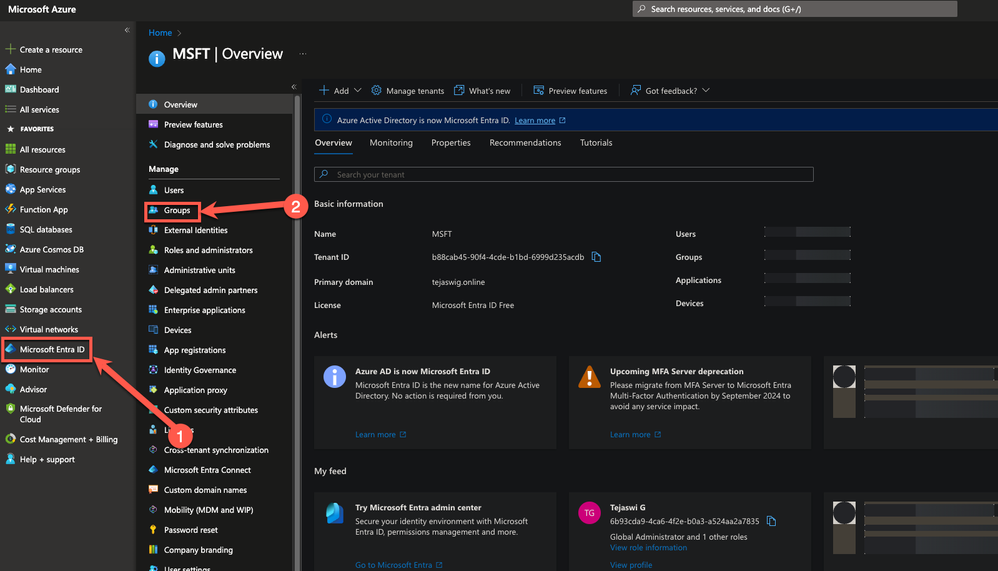
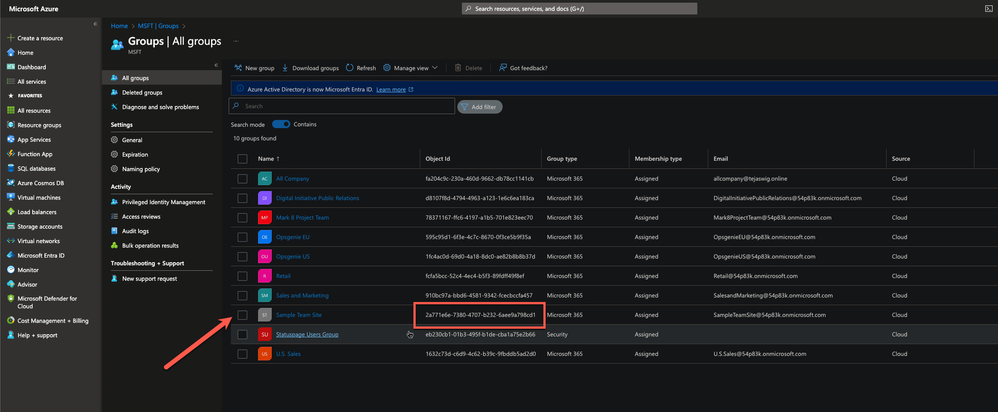
- Now let's find a group we want to map! Navigate to your Microsoft Entra ID and click on groups.
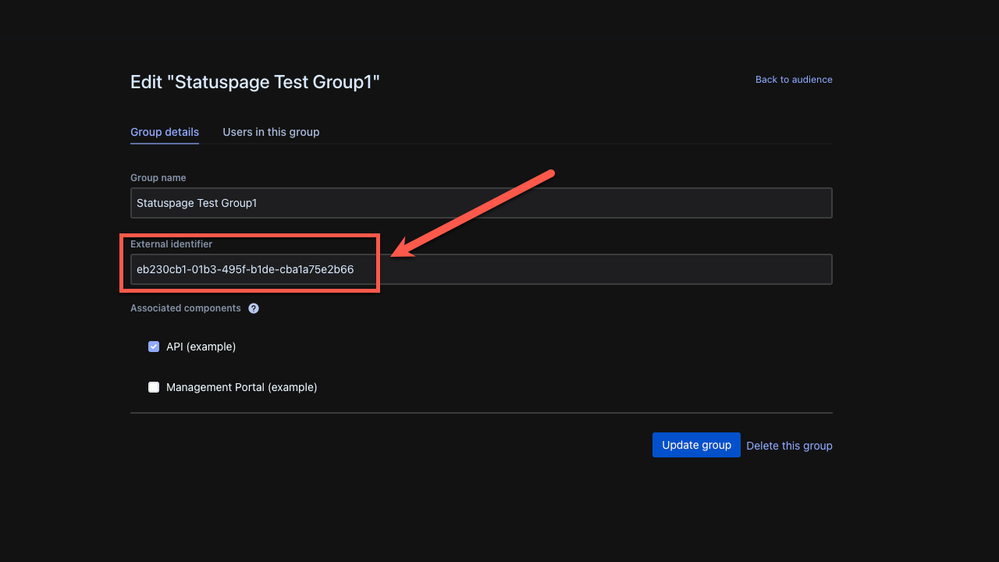
- Copy the ObjectID from the group that you would like to map. This is used as the External identifier in Statuspage
- Past the ID in the External identifier field of the group in Statuspage
- Once the group is mapped, you can start adding members to the group in Microsoft Entra. Any Entra members that have a membership in the group will be reflected in the mapped group in Statuspage.
Now your Entra Users Should be able to see the components in the Statuspage based on thte Groups to which they are assigned to after they login via the SSO.
To make sure we keep offering content that truly benefits you, it would mean a lot to us if you could share whether this article was helpful by giving a thumbs up👍 or down 👎
Additionally, your insights are incredibly valuable in our journey to improve, so please don't hesitate to provide more detailed feedback directly in this community article.
Was this helpful?
Thanks!
Tejaswi G

1 comment