Community resources
Community resources
Community resources
- Community
- Q&A
- Atlassian Guard
- Questions
- Automated User Provisioning and SSO with JumpCloud
Automated User Provisioning and SSO with JumpCloud

This post will demonstrate how to provision users and allow single sign-on (SSO) access into Atlassian Cloud with JumpCloud, an officially supported IdP for Atlassian.
In order to begin there are a few prerequisites to set you up for success including:
- A new or existing Atlassian site
- Verifying your domain
- Subscribe to Atlassian Access
- A JumpCloud account (free up to 10 users and 10 devices)
- SAML workflow requires that the email address be the same between Atlassian and JumpCloud.
Steps 1-3: Walks through how to configure SSO through SAML 2.0
Steps 4-5: Walks through how to configure automatic user provisioning through SCIM
Step 1 - Configure Your Atlassian Cloud Application in JumpCloud
- Login to the JumpCloud admin portal
- Click on ‘SSO’
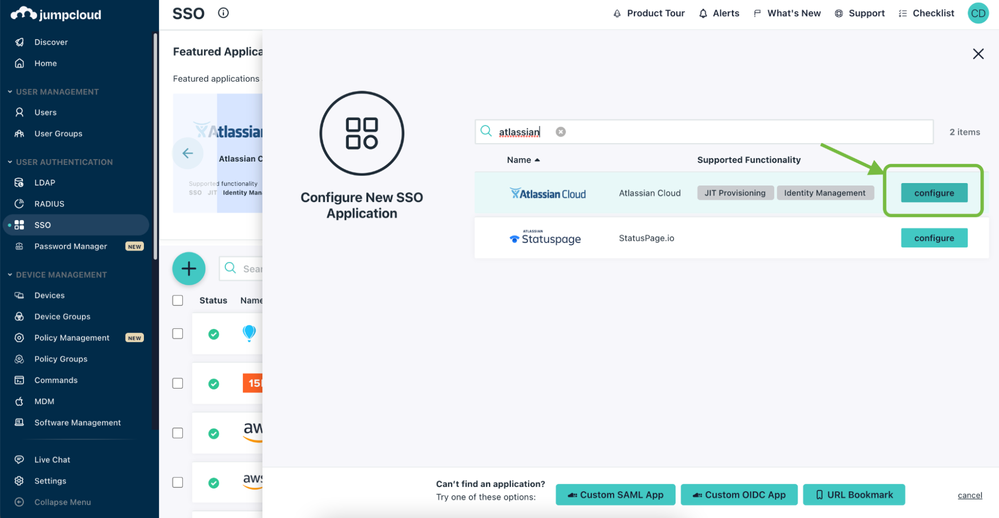
- Click on (+) and search for Atlassian Cloud or select from the featured applications section above
- Click ‘configure’
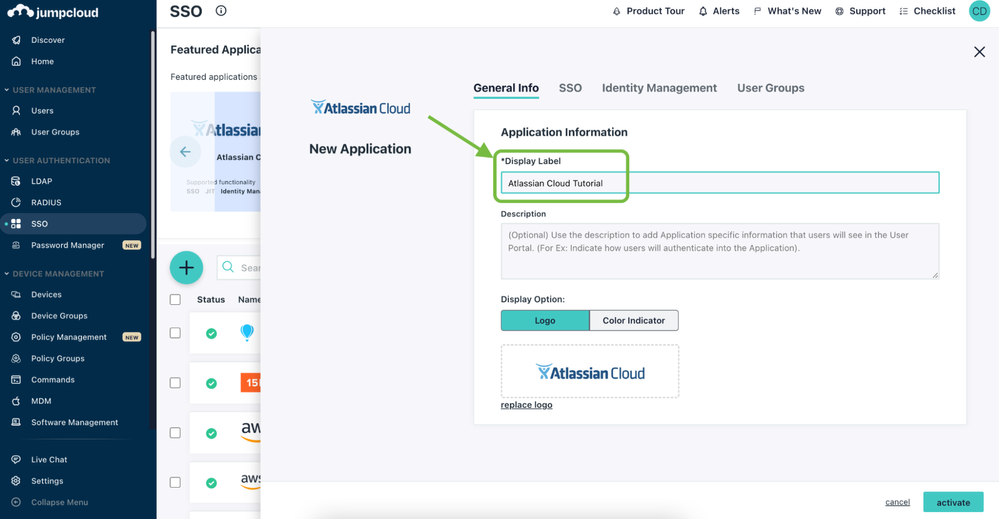
- In the ‘General Info’ section enter a display label that will appear below the icon.
Step 2 - Setting Up SSO in JumpCloud
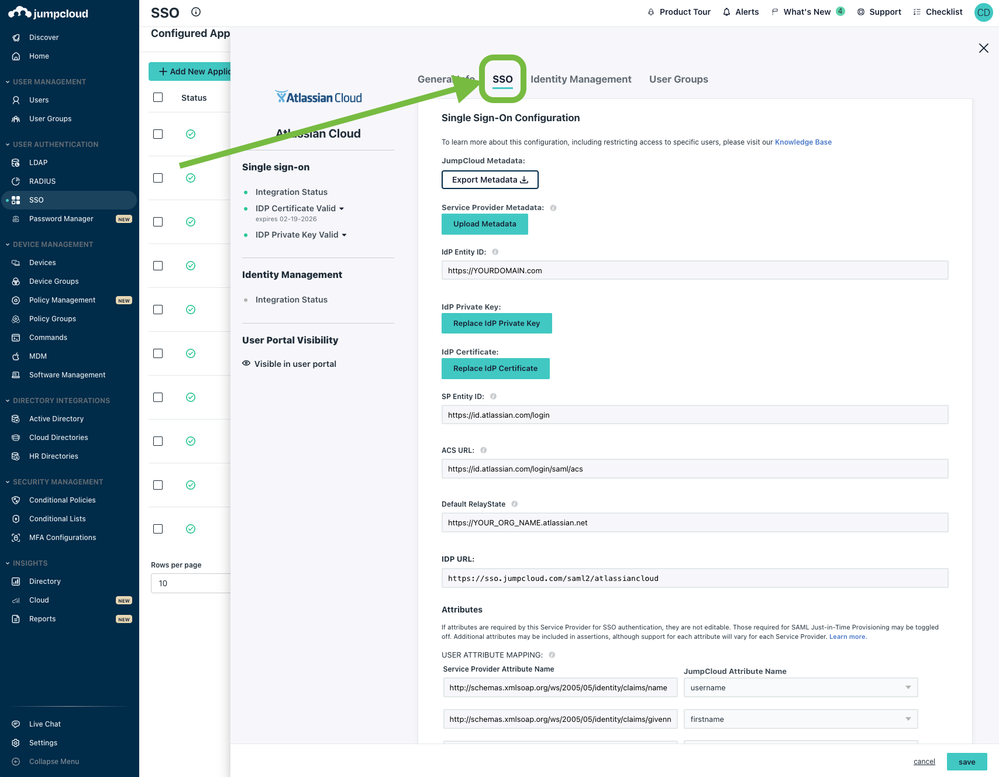
Within the application configuration next click on the ‘SSO’ tab. Here we will configure the SAML 2.0 settings to allow users SSO access in their JumpCloud user portal. To begin:
- In IdP Entity ID, replace YOURDOMAIN with your domain that you have verified.
- For Default RelayState, replace YOUR_ORG_NAME with your Atlassian site domain.
- For the IDP URL, you can replace it with your Atlassian site domain or leave as the default ‘atlassiancloud’
- Then click ‘activate’
- After the application generates the IdP certificate, download the certificate from the upper right hand side of the screen.
- Finally, open the Atlassian connector again and copy the IDP URL for the next step
- Keep this tab open :)
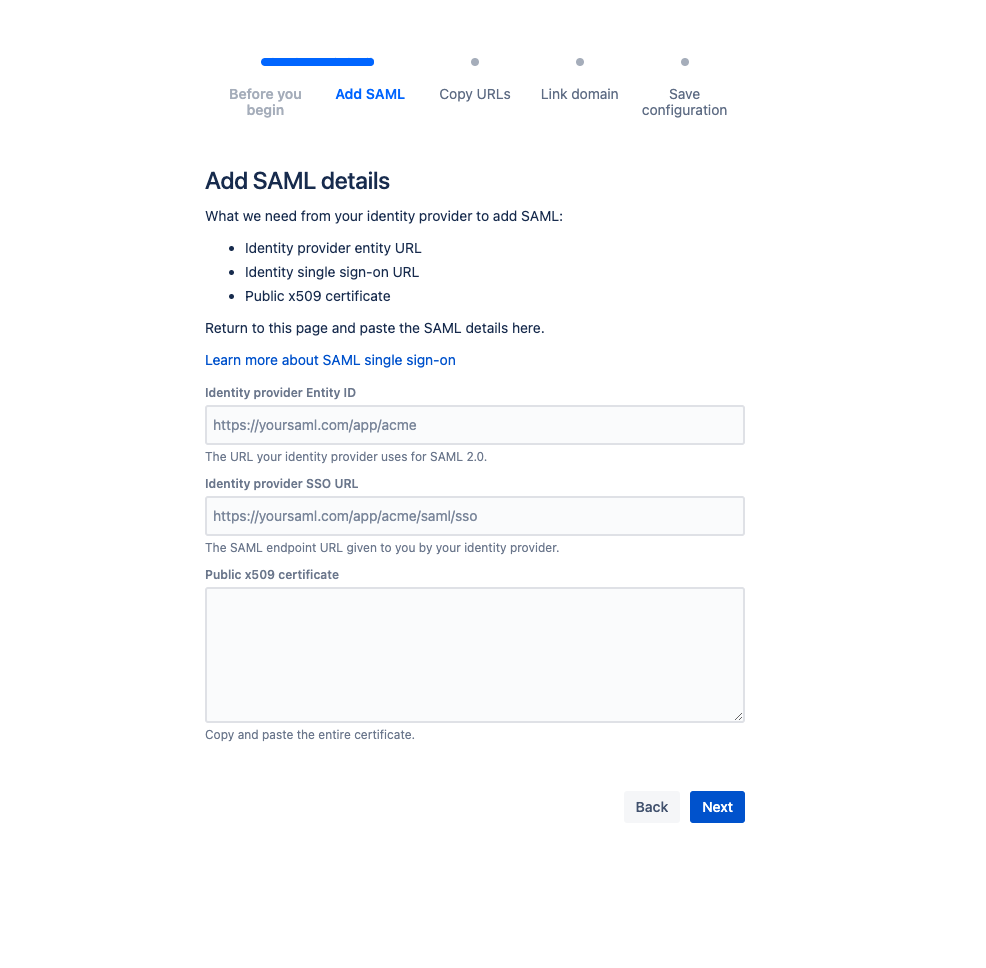
Step 3: Configure Atlassian Access
- Login to the Atlassian admin console.
- Go to Security > SAML single sign-on.
- Click Add SAML configuration.
- In the Identity provider Entity ID field, enter the IdP Entity ID from JumpCloud.
- In the Identity provider SSO URL field, enter the IDP URL from JumpCloud.
- In the Public x509 certificate field, enter the contents of the certificate you downloaded
- You might need to open a plain text/code editor
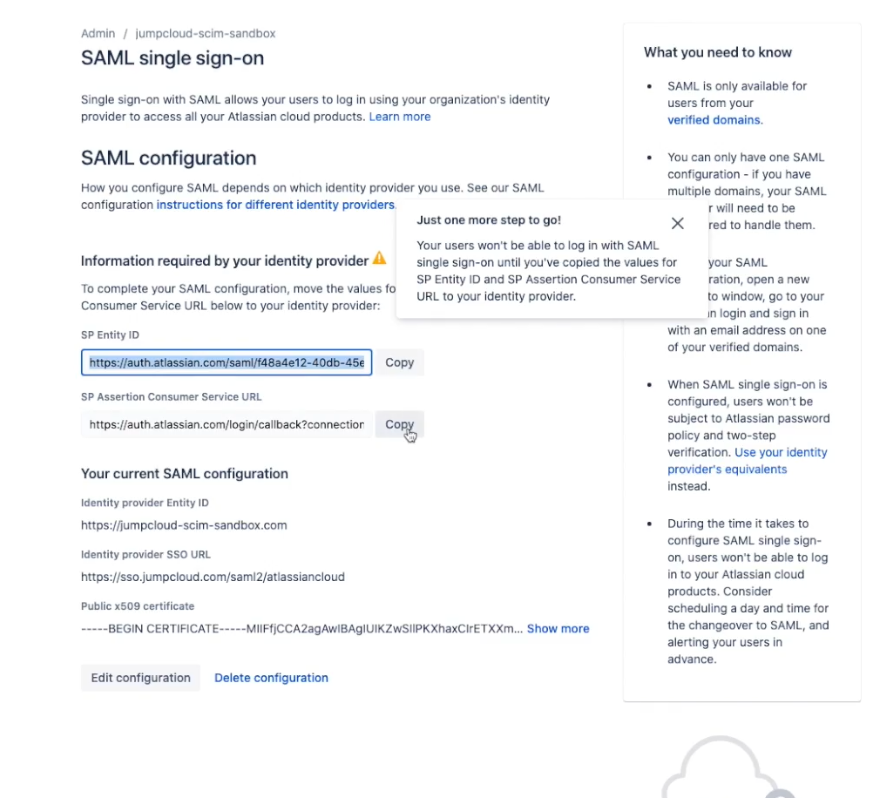
- In the "Information required by your Identity Provider" section, you will see information displayed for:
- SP Identity ID
- SP Assertion Consumer Service URL (ACS URL)
- Copy the SP Identity ID and the SP ACS URL values for use during configuration of the JumpCloud SSO Application Part 2.
- Click save configuration.
- Keep this tab open
Finish Configuring the JumpCloud SSO Application
- Open the Atlassian connector in JumpCloud.
- For SP Entity ID, enter the SP Identity ID from Atlassian.
- For ACS URL, enter the ACS URL from Atlassian.
- Click save.
Step 4: Set Up User Provisioning & De-provisioning
In the Atlassian Admin tab, ensure that you have verified your domain (this can take up to 72 hours to verify).
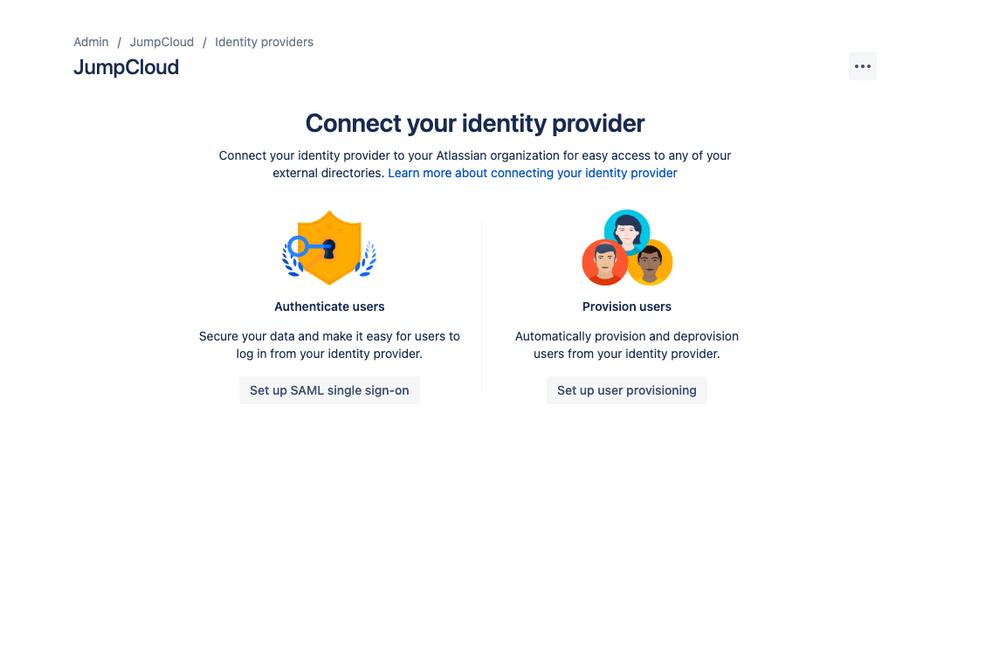
- Click the ‘Security’ tab
- Click the ‘Identity Provider’ tab and then ‘Add Identity Provider’
- Select JumpCloud from the drop down and enter a directory name or just name it ‘JumpCloud’
- Then connect your JumpCloud provisioning by clicking on Provision Users
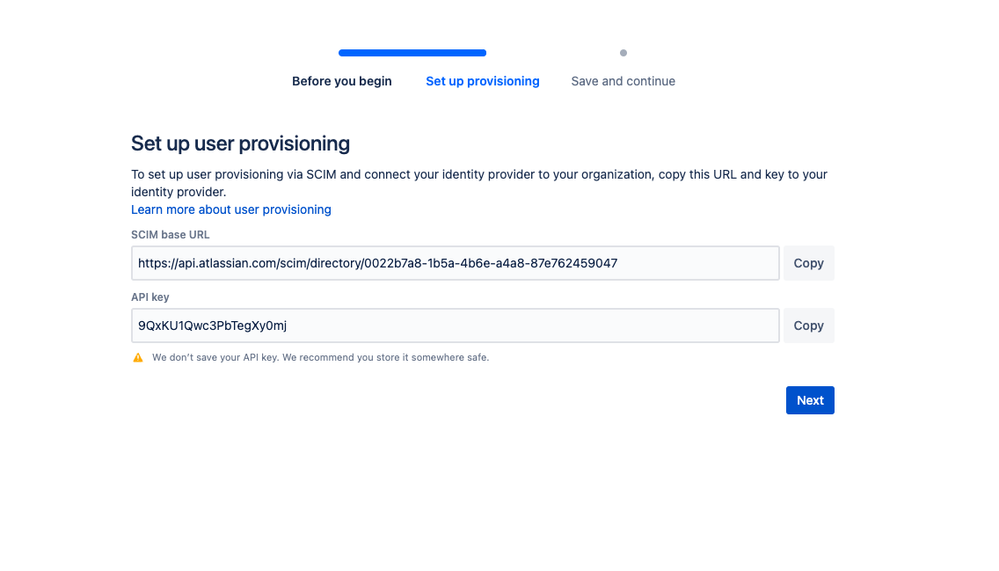
- Copy and paste the two fields of SCIM base URL and API key into your Atlassian connector in JumpCloud under the ‘Identity Management’ field.
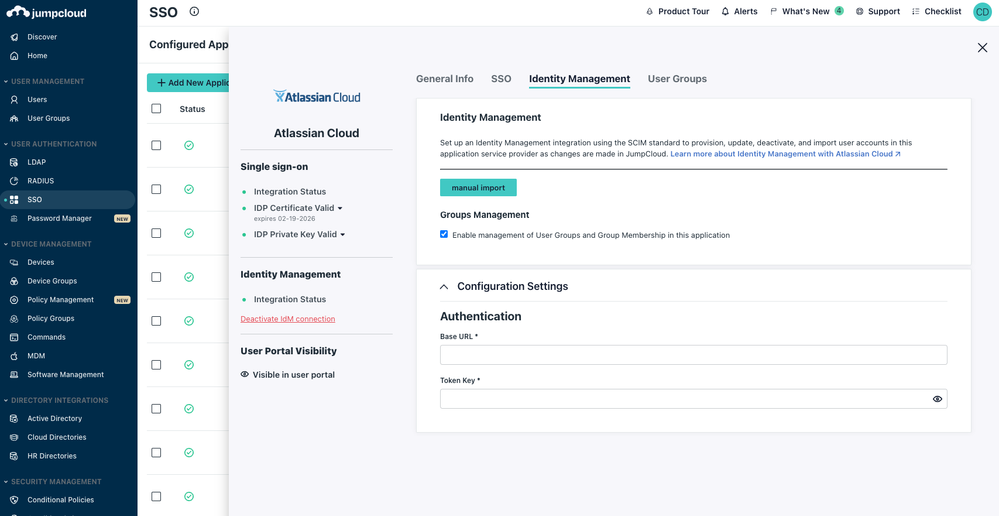
Step 5: Enable Atlassian Identity Management in JumpCloud
- In the Atlassian connector you enabled for SSO, click ‘Enable management of User Groups and Group Membership’ if you want to provision, manage, and sync groups.
- You're presented with two fields:
- SP Base URL: Paste the Directory Base URL you saved when you created the Directory for JumpCloud in Atlassian Cloud
- SP API Token: Paste your Atlassian Cloud API Key
- Click Activate
- You’ll receive a confirmation that the Identity Management integration has been successfully verified and a Public Certificate is created. You can download the certificate from here.
- Click save.
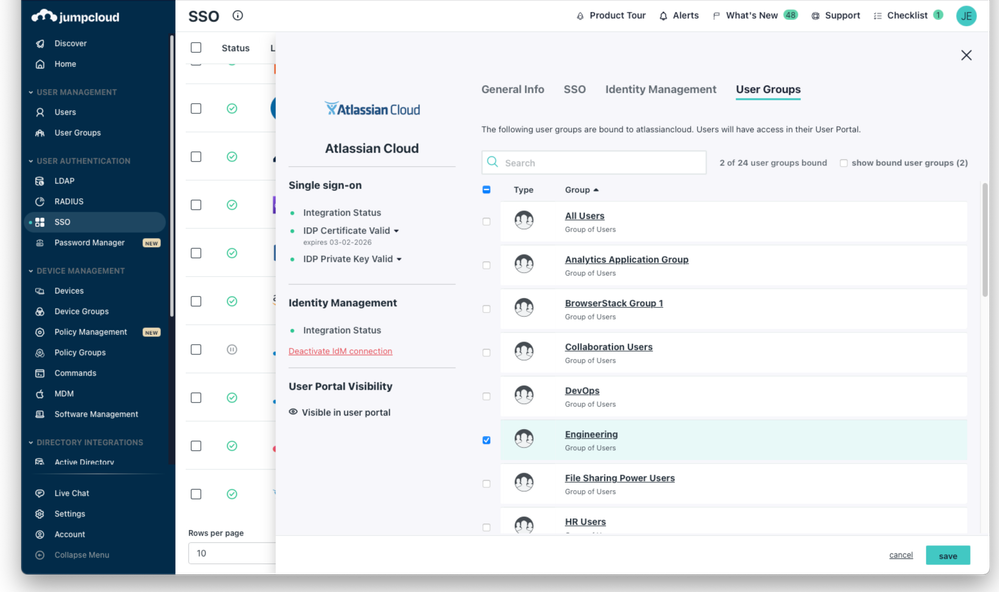
- After the application is saved, it will appear in your SSO Applications list. You can now connect user groups to the application in JumpCloud to provision and provide user access to Atlassian Cloud.
Attribute Mappings
The following table lists attributes that JumpCloud sends to Atlassian Cloud.
JumpCloud Property | JumpCloud UI Attribute Name | Value and Validation in JumpCloud | Atlassian Cloud Attribute |
Company Email | string | emails: value | |
username | Username | string | username |
firstname | First Name | string | name.givenName |
lastname | Last Name | string | name.familyName |
suspended | suspended | boolean | active:false = inactive |
created | Created Date | string | default |
_id | Object ID | string | SCIM user id |
middlename | Middle Name | string | name.middleName |
displayname | Display Name | string | name.displayName |
company | Company | string | organization |
jobTitle | Job Title | string | title |
department | Department | string | department |
addresses: locality |
| string | address |
phoneNumbers: type [=work phone “business”] | Work Phone | string | phone |
phoneNumbers:number | Work Phone | string | phone |