Community resources
Community resources
Community resources
- Community
- Q&A
- Jira Align
- Articles
- Single Sign On (SSO): Configuring Multiple Identity Providers and Transitioning Metadata
Single Sign On (SSO): Configuring Multiple Identity Providers and Transitioning Metadata
The Jira Align SAML 2.0 IdP (Identity Provider) initiated SSO Solution can support multiple identity providers as needed. The following article will cover how to support multiple identity providers and how to transition to a new identity provider or make general modifications to the identity provider metadata.
Supporting Multiple Identity Providers or Multiple Configurations from a Single Identity Provider
- Configure your first Identity Provider SSO Solution as per https://community.atlassian.com/t5/Jira-Align-articles/Video-How-to-enable-single-sign-on-SSO-with-Jira-Align/ba-p/1296205 and https://agilecrafthelp.zendesk.com/hc/en-us/articles/115000374174-10X-Jira-Align-SSO-Support
- Create a second set of IdP metadata in your original IdP or an additional IdP
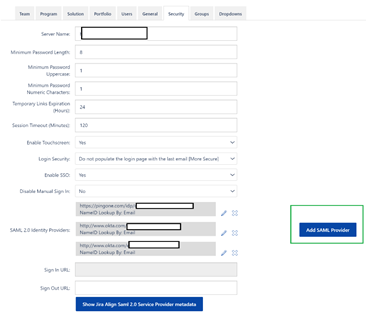
- Navigate to Jira Align Admin > Platform > Security > Click “Add SAML Provider” and paste in the 2nd set of metadata
Notes:
- The “Sign in URL” field will be grayed out until “Disable Manual Sign In” is set to Yes. It is recommended to validate SSO configurations before setting “Disable Manual Sign In” to Yes.
- Jira Align only supports a single “Sign in URL” redirect which means users will need to navigate directly to the sign in URL of additional IdP configurations. A good technique for doing this is users adding the additional IdP configuration sign in URLs to their browser favorites.
Transitioning Metadata for Updates (accounting for the agilecraft.com to jiraalign.com domain change).
Option 1:
- Have your SSO engineer create a new SAML 2.0 SSO configuration in your IdP utilizing your new site URL as the Entity ID and Assertion Consumer Service Location.
- If the original Entity ID and Assertion Consumer Service Location you utilized for SSO was https://www.customer.agilecraft.com the new value for Entity ID and Assertion Consumer Service Location would be https://www.customer.jiraalign.com. Ensure that the SAML signature policy is set to sign both the Response and Assertion.
- Copy the newly created Jira Align IdP metadata and navigate to Jira Align Admin > Platform > Security > Click “Add SAML Provider” and paste in the newly created Jira Align metadata
- Validate the newly created Jira Align domain SSO configuration using the sign in URL from your identity provider
- When ready to transition replace the *agilecraft.com “Sign in URL” under Jira Align Admin > Platform > Security with the newly created jiraalign.com sign in URL.
- Revalidate the SSO solution and remove the original *agilecraft.com metadata from Jira Align Admin > Platform > Security
Option 2:
- Have your SSO engineer update the existing SSO SAML configuration by replacing the agilecraft.com Entity ID and Assertion Consumer Service Location URL with the jiraalign.com domain
- Validate the SSO solution now authenticates into the jiraalign.com domain
Notes: If Manual login is disabled and SSO is reconfigured to the jiraalign.com domain name, any links to the agilecraft.com domain such as Jira weblinks or links within email notifications will only work if your SSO solution has a proper relay state configured. The Jira Align team is currently working on a solution to mass update Jira weblinks. In the meantime customers can request a redirect from the agilecraft.com to the jiraalign.com domain after re-configuring their SSO solution in case of any legacy agilecraft.com links.
Was this helpful?
Thanks!
Tim Keyes

About this author
Program Manager
Atlassian
16 accepted answers
2 comments